MICROSIMULATIONS
Build cyber response
muscle memory
Build cyber response muscle memory
Deliver an impactful experience that is a hit from day one, with Cyber Fundamentals
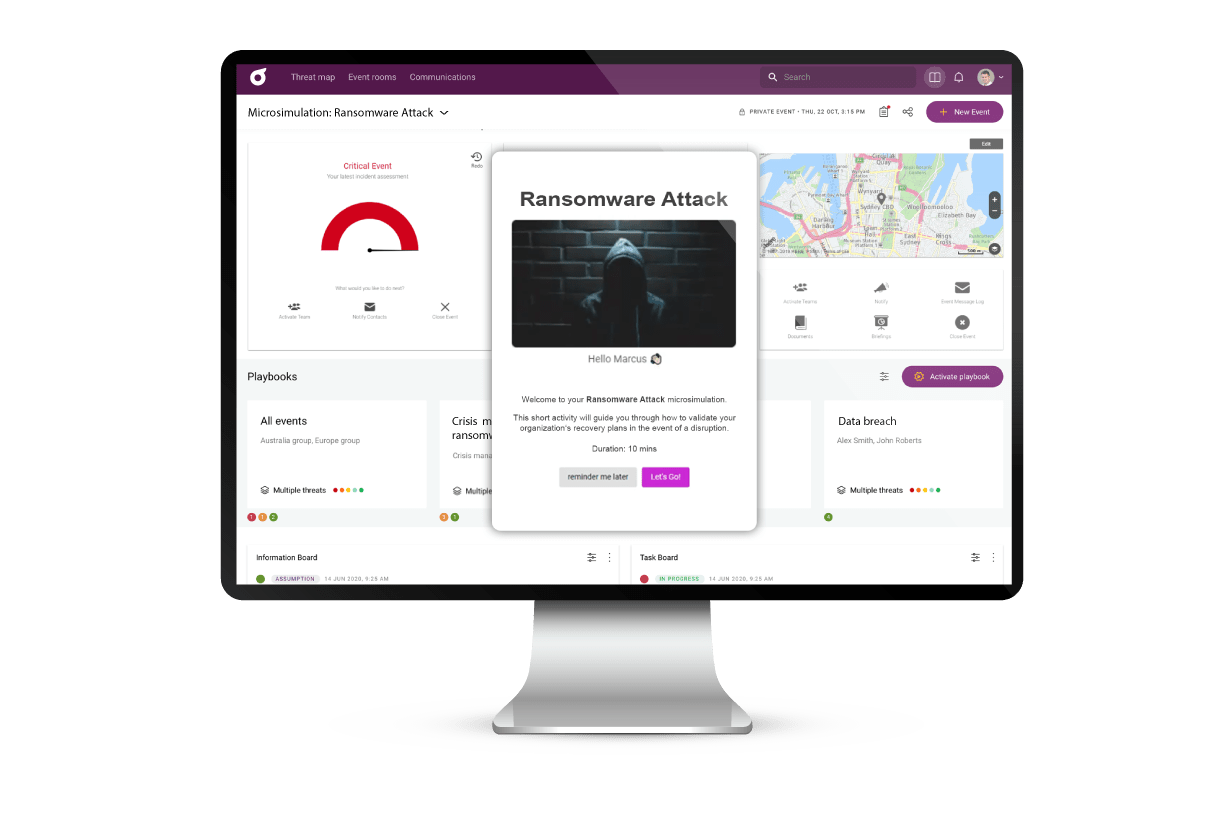


Take the complexity out of cyber resilience learning with a Cyber Microsimulations package
From ransomware to digital supply chain attacks, it’s only a matter of clicks before your network is compromised. Yet, despite the increasing frequency of cyber-attacks, many organizations lack the capability to respond.
Leaders planning traditional cyber response activities like tabletop exercises are finding them time and resource intensive. That’s where Cyber Fundamental Microsimulations can help.
Requiring zero integration and purpose-built to meet the needs of your entire team, Cyber Fundamentals have been designed to deliver an impactful experience that is a hit, from day one.
Ready to get started?
Take the complexity out of cyber resilience learning with a Cyber Microsimulations package

From ransomware to digital supply chain attacks, it’s only a matter of clicks before your network is compromised. Yet, despite the increasing frequency of cyber-attacks, many organizations lack the capability to respond.
Leaders planning traditional cyber response activities like tabletop exercises are finding them time and resource intensive. That’s where Cyber Fundamental Microsimulations can help.
Requiring zero integration and purpose-built to meet the needs of your entire team, Cyber Fundamentals have been designed to deliver an impactful experience that is a hit, from day one.
Ready to get started?
Microsimulations included in Cyber Fundamentals

1. Incident Assessment
Participants will:
Mobilize a team to confirm whether a cyber breach has compromised your company’s ecosystem, and deploy protocols to contain and limit further exposure.

2. Assess Impact Severity
Participants will:
Identify customers, services, products, processes and assets impacted by the incident, as well as those of your third parties.
.

3. Map Stakeholders and Plan Communication
Participants will:
Prioritize response and designate authority. They will be asked to identify internal and external stakeholders, and establish what information needs to be shared, when, and how.

4. Respond and Recover
Participants will
Activate response teams and playbooks. Delegate responsibilities. Restore systems and associated processes, services, and products.
Sample tasks.

5. Coordinate with Third Parties
Participants will:
Collaborate with third parties to contain damage, mitigate issues, and preserve evidence.
.

6. Communicate
Participants will:
Develop confidence to maintain ongoing communications with stakeholders about what has happened, the impact, steps being taken, and available support.
Microsimulations included in Cyber Fundamentals
Participants will:
Mobilize a team to confirm whether a cyber breach has compromised your company’s ecosystem, and deploy protocols to contain and limit further exposure.
Participants will:
Identify customers, services, products, processes and assets impacted by the incident, as well as those of your third parties.
Participants will:
Prioritize response and designate authority. They will be asked to identify internal and external stakeholders, and establish what information needs to be shared, when, and how.
Participants will
Activate response teams and playbooks. Delegate responsibilities. Restore systems and associated processes, services, and products.
Participants will:
Collaborate with third parties to contain damage, mitigate issues, and preserve evidence.
Participants will:
Develop confidence to maintain ongoing communications with stakeholders about what has happened, the impact, steps being taken, and available support.














